Certego has always promoted and supported Open Source Development culture. Some of us are active members of the Honeynet Project and have contributed to some famous open source tools like Cuckoo Sandbox or Thug.
With the goal to help the security community to fight cyber threats, we have released two new projects this year: Intel Owl to aid cyber threat intelligence operations and Pcapoptikon2 to help analysts with writing IDS signatures.
Meanwhile we have been focusing our research on finding new ways to analyze complex malware. Our own Simone Berni has been working on the development of a new open source tool and just recently, also thanks to his work, its first 1.0 version was released: Qiling, an advanced binary emulation framework.
On the 25th April 2020, Simone had the opportunity to show the results of his work at the famous Hack In The Box Security Conference together with the Qiling creator, Lau Kai Jern.
HITB Conference: Technical details
Qiling is an advanced binary emulation framework that supports Windows, MacOS, Linux and BSD.
Written in Python and based on Unicorn Engine, Qiling is designed to provide high level APIs and fine-grain instrumentation, allowing you to place hooks at every level.
Certego chose to help the development of Qiling with Simone Berni's work.
During his presentation, Simone showed how it is possible to use Qiling as a sandbox to analyze arbitrary malware.
In particular, he prepared two different demo scenarios: Al-khaser and Gandcrab.
Al-Khaser Demo
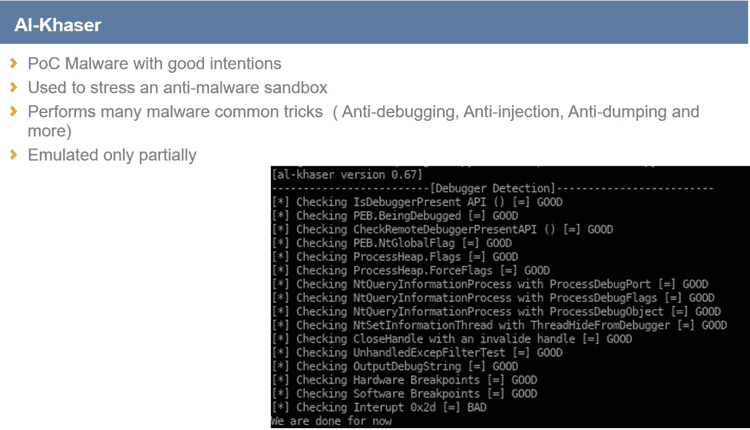
The first scenario is a POC malware application that aims to stress an anti-malware system by checking if the sandbox is fortified and stealthy enough.
During the emulation of Al-khaser, it is possible to understand two things mainly: how stealthy Qiling is and how much it is easy to use. Not everything of Al-khaser has been emulated, Simone implemented only the debugger detection task.
Moreover, Qiling does not pass every single test made by Al-khaser (it passes 85% of checks) but the developers are working on them even right now.
The second point of this demonstration is to understand how we can use Qiling to perform a deep analysis: for example, the emulation of the function that prints the output had an issue: thanks to the API offered by Qiling, Simone was able to replace this function entirely with just 3 lines of code, thus obtaining the expected outputs.
Al-Khaser Demo
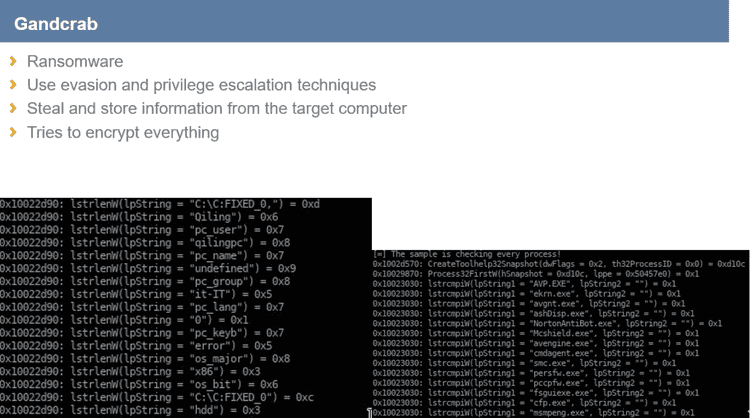
Here, we are talking about a famous ransomware, which is very interesting because it uses different sandbox evasion techniques before executing itself.
The demo of Gandcrab shows how powerful Qiling can be when used as a sandbox. Simone, during his work, implemented the concept of "Profiles", later extended by the Qiling team, and the core feature to analyze malware.
The profile is just a configuration file that describes everything about the emulation: it started as a simple file containing only the Windows version that Qiling has to emulate; later, it was extended to contain information about the Volumes, Drives, Permissions and Network configuration. Now it is possible to have a profile for every OS (Linux, BSD e MacOS are supported), and it is even possible to change the emulation parameters from this config file.
Simone demonstrated how much information it is possible to retrieve thanks to Qiling during the analysis of a ransomware like Grandcrab: every registry accessed is stored, every "printf" is saved (so it is possible to retrieve memory that has been copied from one place to another), every syscall and kernel call is stashed for future analysis. With a little bit more details, he explained how Gandcrab tries to retrieve every piece of information about the victim machine and how the malware stores the stolen information.
At the end of the demo, Simone shows how it is possible to change the Profile to change the behaviour of Gandcrab.
For example, you can change its permissions: when Gandcrab is executed as a user, it will spawn a shell to re-execute itself as administrator.
Another strange behaviour Simone discovered can be observed when you apply a russian keyboard layout in Qiling. Again, this is possible to do so by simply adding a registry key and the desired value to the profile. When executed in an environment that has a russian keyboard, Gandcrab would kill itself.
Conclusions
Qiling is a powerful tool, continuously developed and improved every single day: in the future it will be a common framework that malware analysts have to be familiar with.
Certego will continue to contribute to this project to improve the chances of everyone in fighting malware.