We are proud to announce that Certego has joined the community of Contributors to VirusTotal, the biggest aggregator of antivirus engines and website scanners.
VirusTotal is a free service that everyone can use to check for virus or threats in a file, URL, domain or IP address by leveraging more than 70 antivirus scanners, blacklisting services and analysis tools provided by the global security vendors. Founded in 2004 by a Spanish company, VirusTotal was acquired by Google in 2012 and, in 2018, the ownership switched to Chronicle, a subsidiary of Alphabet.
Starting from this week, most of the intelligence data generated by Quokka, the Threat Intelligence Platform developed by Certego, is available to the VirusTotal community.
The Quokka platform was designed by a team of experienced malware analysts with passion and a strong commitment. The Threat Intelligence Team has mixed different tools, including Honeypots, real “traps” for the cyber criminals, and Sandboxes, virtual environments where it is possible to execute and study malware automatically and at scale. The result is a platform that enables Certego to gather relevant information in real time to track cyber criminal activities.
Additional technical details
We would like to show some examples of what kind of information users can find by leveraging together the power of VirusTotal multi scan engine and the Certego Intelligence information.
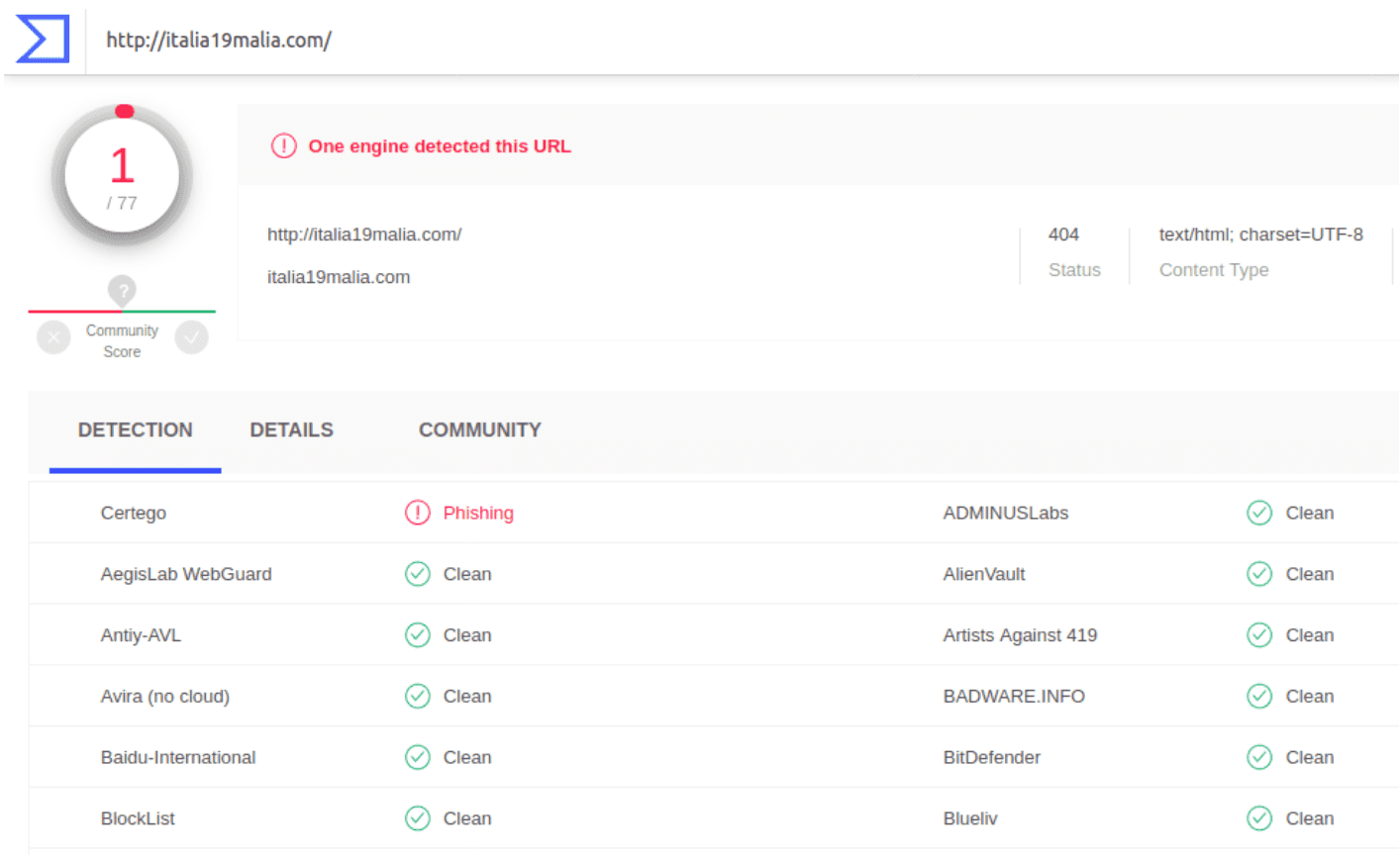
You could be a tech guy or not. In both cases, it surely happened that you found a strange link inside a suspicious email you received and you wanted to verify it before clicking it. One way could be to go to the VirusTotal website, select the URL scan, insert the suspicious link in the input bar and ask for an analysis.
After some seconds, you would find the results of the analysis. For this specific example, the Certego engine detected the URL as containing “Phishing”.
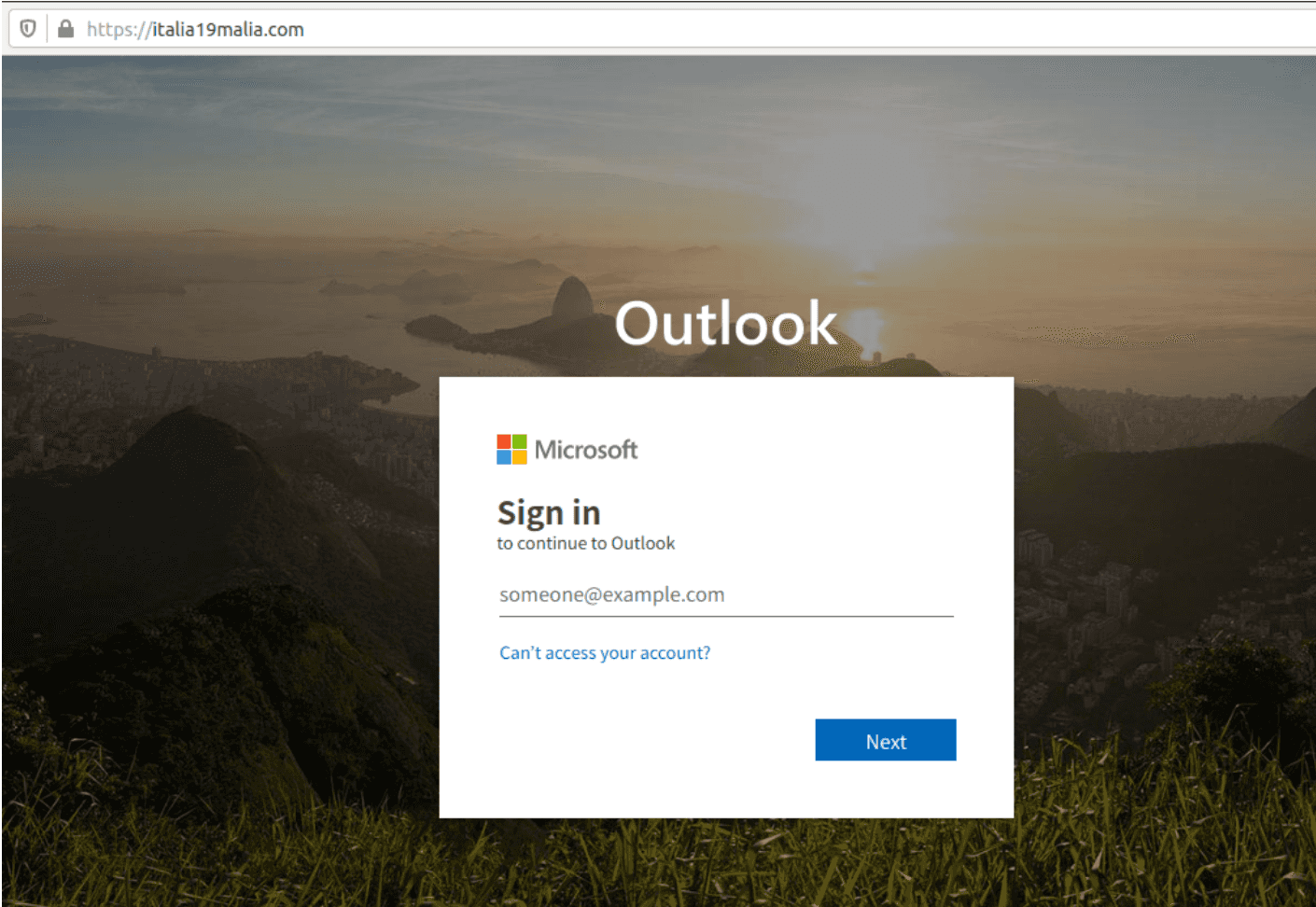
This evaluation helps the end user because, if he had visited the site, he would have found an Outlook account phishing page identical to the real one.
Other than “Phishing”, there are other possible evaluations that can be found after an URL analysis.
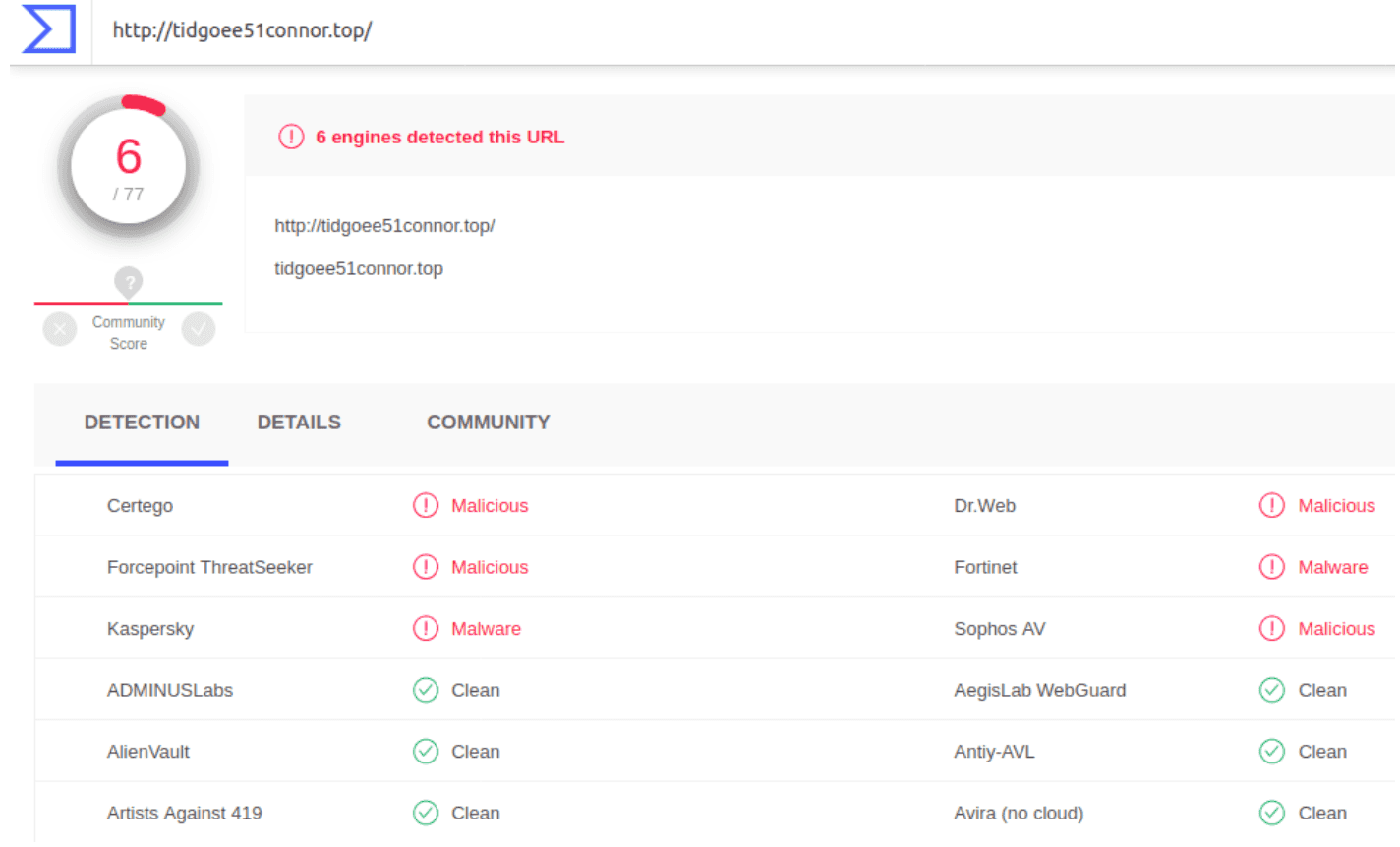
The “Malicious” and “Malware” detection are used to notify if a specific URL or domain was observed to serve malware or simply it was involved in cyber crime activities. Example:
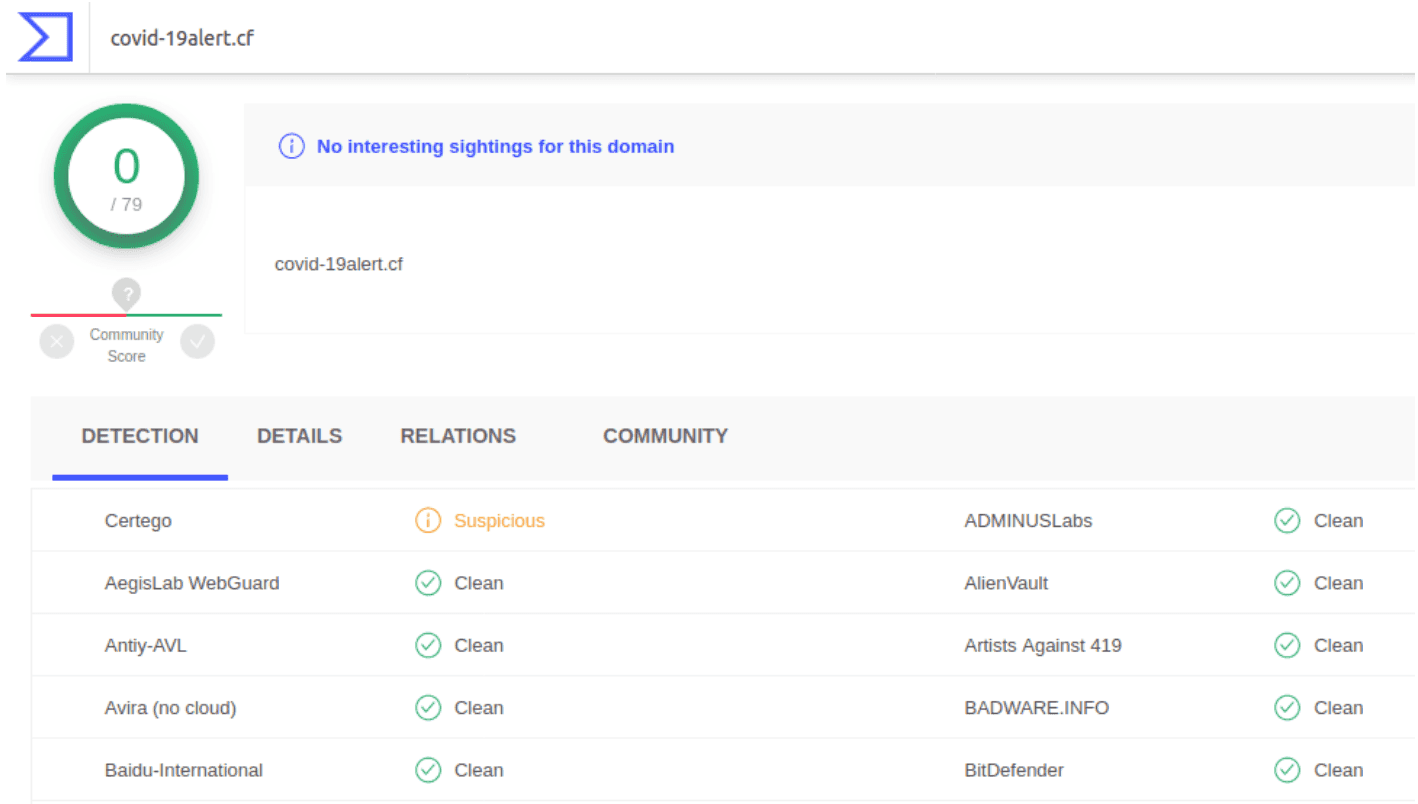
The “Suspicious” detection is used to notify when a specific URL or domain is or was probably involved in malicious activities. For these cases, the engine does not have a clear evidence so it just suggests that the site should be avoided as a precaution. Example:
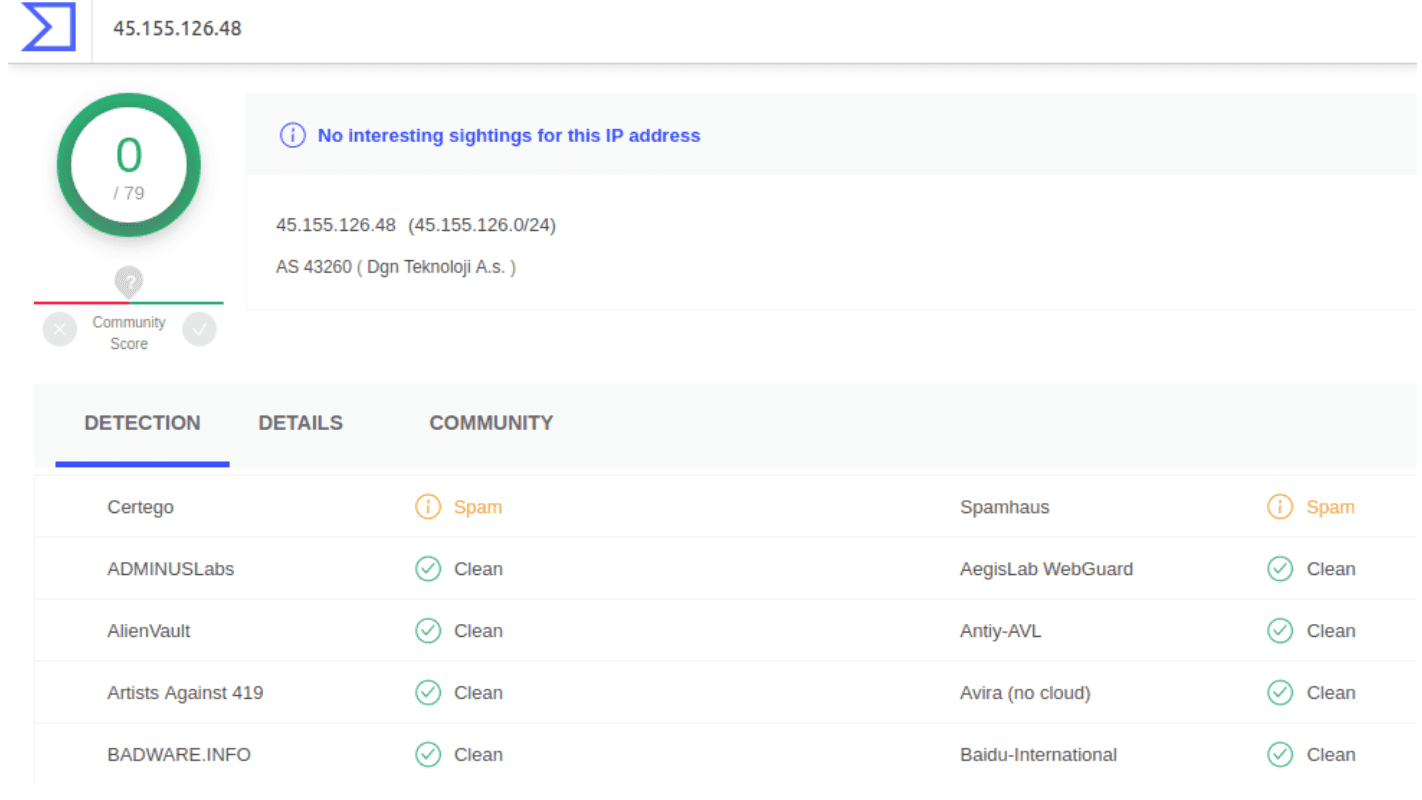
The last case is the “Spam” detection that is used to notify when a specific URL or domain was embedded inside a lot of emails that were sent massively to many inboxes so it is a link that you probably do not want to click. Otherwise, IP addresses are tagged as “Spam” when they have been observed to send a lot of spam, so they are probably related to the presence of a spambot. Example: